🛡️ Cloud Security Mastery
Picture this: You’ve just moved your most precious belongings into a shiny new apartment building. It’s got all the modern amenities, top-notch facilities, and promises of 24/7 security. But here’s the twist—you’re sharing this building with thousands of other residents, and some of them might not be as trustworthy as you’d hope. Welcome to the wild, wonderful, and sometimes worrying world of cloud security!
In 2024 alone, 61% of organizations experienced a cloud security incident, and cloud-based attacks increased by a staggering 95%. But don’t panic! Just like learning to protect your physical home, mastering cloud security is all about understanding the rules of the game and having the right tools in your digital toolkit.
🎯 Ready to transform from a cloud security rookie into a digital guardian? Let’s embark on this adventure together!
🏰 Welcome to Your Digital Kingdom: Understanding the Cloud Security Landscape
Think of cloud security as protecting a magnificent digital kingdom. Just like medieval castles needed multiple layers of defense—moats, walls, guards, and secret passages—your cloud infrastructure needs comprehensive protection strategies. The difference? Instead of protecting against knights and catapults, we’re defending against hackers, malware, and data thieves.
But here’s where it gets interesting. Unlike owning your own castle where you control everything, cloud security operates on what experts call the “shared responsibility model.” It’s like living in a luxury high-rise where the building management handles the structure, elevators, and common areas, while you’re responsible for securing your own apartment.

🚨 The Current State of Cloud Security
📊 2024 Cloud Security Reality Check:
- Nearly 5x more daily cloud alerts compared to early 2024
- 116% increase in “impossible travel” security events
- $4.4 million average cost per data breach
- 91 days average time to fix malware in cloud storage
💡 Now that we understand the stakes, let’s dive into the fundamental principles that’ll keep your digital kingdom secure…
🤝 The Shared Responsibility Model: Your Cloud Security Partnership
Imagine you’re staying at a five-star hotel. The hotel takes care of the building’s security, fire safety systems, and structural integrity. You, however, are responsible for locking your room, keeping your valuables safe, and not leaving your keycard lying around. This is exactly how cloud security works!
The shared responsibility model divides security duties between you (the customer) and your cloud provider. Understanding this division isn’t just helpful—it’s absolutely critical. As one industry expert puts it: “99% of cloud security failures will be the customer’s fault through 2025.” Ouch! But the good news? Most of these failures are completely preventable.
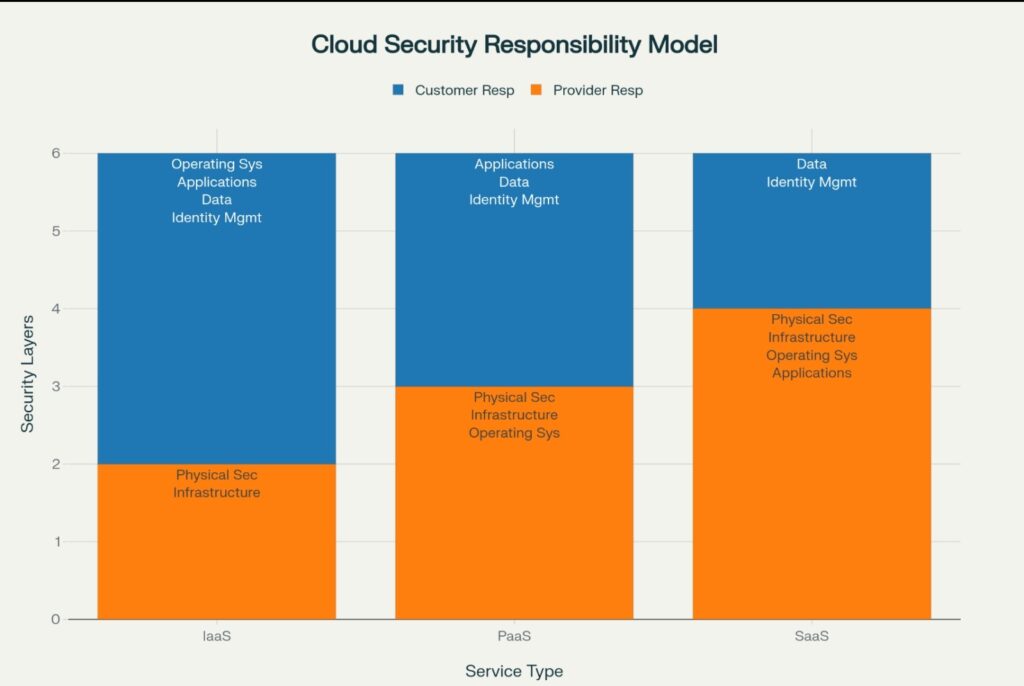
🏗️ Breaking Down the Responsibility Layers
🔧 What Your Cloud Provider Handles:
- Physical Security: Data centers, servers, and hardware protection
- Infrastructure: Networks, host operating systems, and virtualization layers
- Platform Services: Managed databases, container orchestration, and serverless functions
👤 What YOU’RE Responsible For:
- Data Protection: Encryption, backup, and classification
- Identity Management: User access, passwords, and permissions
- Application Security: Code vulnerabilities and secure configurations
- Network Controls: Firewalls, traffic encryption, and network segmentation
🔍 Think of this partnership like a dance—when both partners know their steps, the performance is flawless. Now, let’s explore the biggest threats lurking in our digital kingdom…
👹 Meet the Digital Villains: Top Cloud Security Threats in 2025
Every great kingdom has its enemies, and your cloud environment is no exception. Let’s meet the main antagonists in our cloud security story—and more importantly, learn how to defeat them!
🎭 Threat #1: The Misconfiguration Menace
Picture leaving your front door wide open with a sign saying “Welcome, thieves!” That’s essentially what security misconfigurations do. They’re the #1 cloud security threat in 2024, responsible for countless breaches. These sneaky villains include:
- Open Storage Buckets: Like leaving your photo albums on the street corner
- Overpermissive Access: Giving everyone in town keys to your house
- Unencrypted Data: Writing your secrets in plain sight
- Missing Security Updates: Using a rusty lock from the 1990s
🕵️ Threat #2: The Identity Impostor
Remember the 2024 Snowflake breach that affected AT&T, Ticketmaster, and 165 other organizations? The culprit was stolen credentials without multi-factor authentication. The attacker simply used legitimate login details to waltz right into systems, causing over $2 million in damages.
🚨 Real-World Example: The Snowflake incident showed how attackers used info-stealer malware to harvest credentials from employee devices, then accessed cloud platforms months later. The scariest part? Most affected accounts lacked basic MFA protection!
🤖 Threat #3: The AI-Powered Adversary
As if regular hackers weren’t enough, now we have AI-enhanced attacks! These digital villains use artificial intelligence to:
- Generate more convincing phishing emails
- Automatically discover vulnerabilities
- Adapt attack strategies in real-time
- Scale attacks across thousands of targets simultaneously
⚔️ Now that we know our enemies, it’s time to build our defenses. Let’s explore the mighty weapons in our cloud security arsenal…
🛡️ Your Digital Armor: Essential Cloud Security Strategies
🔐 Strategy #1: The Encryption Fortress
Think of encryption as your data’s personal bodyguard—one that speaks in secret codes only you understand. When data is encrypted, it looks like gibberish to anyone without the key. Even if hackers steal your data, they’ll just have a bunch of meaningless scrambled text.
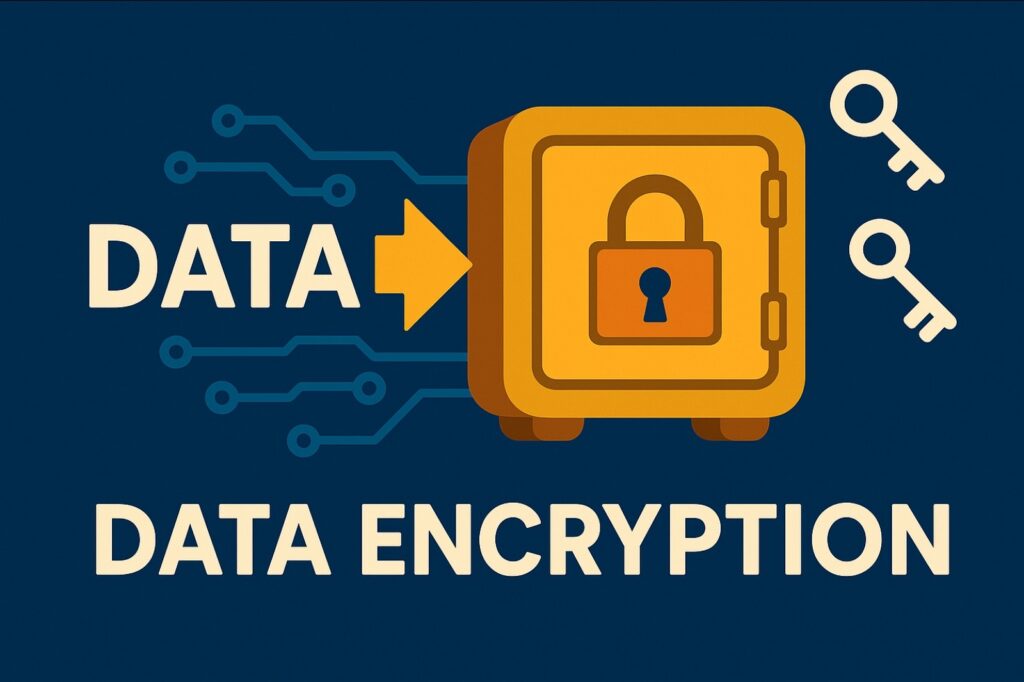
Encryption works in three crucial scenarios:
- Data at Rest: Like locking your valuables in a safe when you’re not using them
- Data in Transit: Like sending messages in secret code while they travel
- Data in Use: Like having confidential conversations in a soundproof room
💡 Pro Tip: Use AES-256 encryption (the gold standard) and always manage your encryption keys separately from your data. It’s like keeping your safe key in a different location from your safe!
🚪 Strategy #2: The Multi-Factor Authentication Gate
Remember those movies where getting into a high-security vault requires multiple people with different keys, plus fingerprint scans, plus secret codes? That’s exactly what multi-factor authentication (MFA) does for your digital accounts!
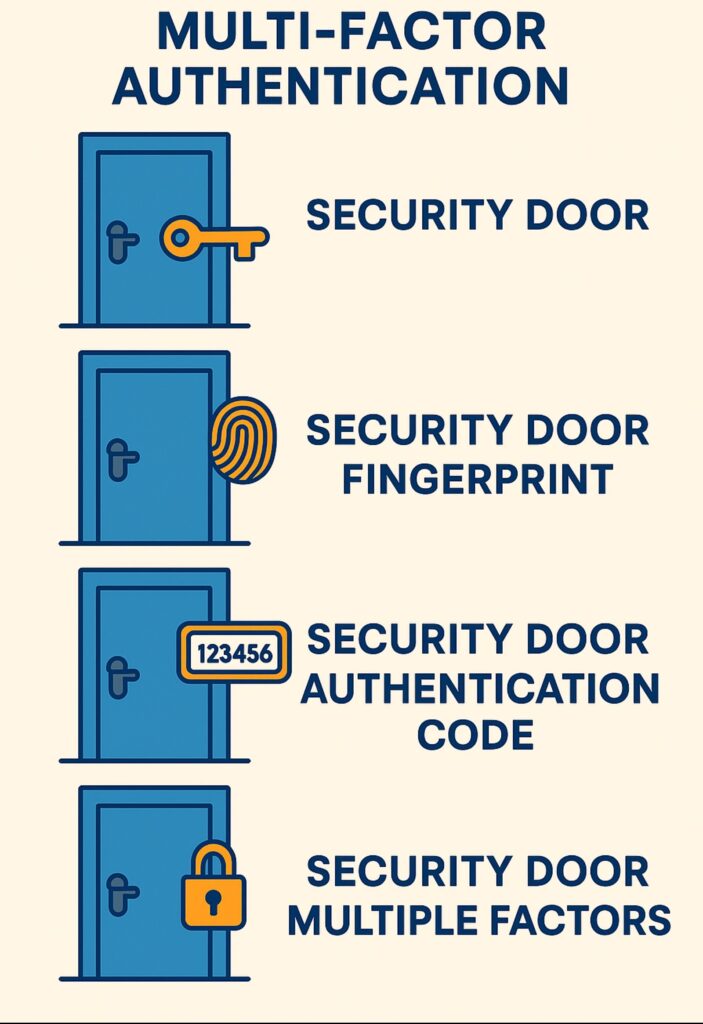
MFA combines three types of proof:
- Something you know (like a password)
- Something you have (like your phone or a security token)
- Something you are (like your fingerprint or face)
🎯 MFA Impact: Enabling MFA blocks 99.9% of automated attacks. It’s like having a bouncer at your digital door who actually knows what they’re doing!
🕸️ Strategy #3: The Zero Trust Web
“Never trust, always verify”—that’s the motto of Zero Trust security. Instead of assuming everyone inside your network is friendly (like trusting all hotel guests just because they have room keys), Zero Trust treats everyone as potentially suspicious until proven otherwise.
This approach has become essential because the traditional security perimeter has dissolved. With employees working from coffee shops, using personal devices, and accessing cloud services from anywhere, the old “castle and moat” security model simply doesn’t work anymore.
“In the cloud, there’s no perimeter. You’re dealing with decentralized services, ephemeral workloads, and identities that operate at massive scale. Zero Trust helps you regain control, even in elastic, multi-cloud infrastructure.”
🔧 These foundational strategies are just the beginning. Let’s dive deeper into the advanced tools that security professionals use to protect enterprise cloud environments…
🎮 Level Up: Advanced Cloud Security Tools and Frameworks
🎯 CSPM: Your Cloud Security Scout
Cloud Security Posture Management (CSPM) is like having a dedicated security guard who constantly patrols your cloud environment, checking every door, window, and potential entry point. CSPM tools automatically scan for misconfigurations, compliance violations, and security gaps across all your cloud resources.
These digital scouts provide:
- Continuous monitoring of your cloud infrastructure
- Real-time alerts when something looks suspicious
- Compliance reporting to meet industry standards
- Remediation guidance to fix issues quickly
🚀 CNAPP: The Ultimate Security Suite
If CSPM is a security guard, then Cloud-Native Application Protection Platform (CNAPP) is like having an entire security team with specialized skills. CNAPP combines multiple security tools into one comprehensive platform, offering:
🛠️ CNAPP Components:
- CSPM: Configuration and compliance monitoring
- CWPP: Workload protection for containers and VMs
- CIEM: Identity and access rights management
- DSPM: Data security and privacy protection
- IaC Scanning: Security checks during development
📋 Security Frameworks: Your Digital Constitution
Just like countries have constitutions that outline fundamental laws, cloud security frameworks provide structured guidelines for protecting your digital assets. The most popular frameworks include:
- NIST Cybersecurity Framework: The comprehensive approach loved by government agencies
- Cloud Security Alliance (CSA) Controls: Specifically designed for cloud environments
- ISO 27001: The international standard for information security
- CIS Controls: Practical, prioritized security actions
💼 Understanding these tools is great, but let’s see how they work in practice. Time for some real-world scenarios…
🎭 Real-World Cloud Security Scenarios: Learning from 2024’s Biggest Breaches
📱 Case Study 1: The Ticketmaster Takedown
In May 2024, entertainment giant Ticketmaster fell victim to a massive breach affecting 40 million customers. The attack wasn’t the result of some sophisticated hacking technique—it was a simple case of compromised credentials accessing their Snowflake cloud hosting account.
🔍 What Went Wrong:
- Attackers used stolen employee credentials from info-stealer malware
- No multi-factor authentication on critical accounts
- Insufficient monitoring of cloud access patterns
- Over-permissioned accounts with broad data access
✅ How to Prevent This:
- Enable MFA on ALL cloud accounts (no exceptions!)
- Implement Zero Trust network access
- Monitor for “impossible travel” login patterns
- Apply principle of least privilege access
- Regular credential rotation and monitoring
🏥 Case Study 2: The Healthcare Security Crisis
The Community Clinic of Maui faced a devastating ransomware attack in 2024, affecting 123,000 patients. The clinic had to close for two weeks, with nurses using paper charts for weeks afterward. This incident highlights the real-world consequences of cloud security failures.
The attack succeeded because of:
- Inadequate backup and recovery procedures
- Insufficient network segmentation
- Missing endpoint detection and response tools
- Lack of incident response planning
🎓 These real-world examples show us that cloud security isn’t just about technology—it’s about people, processes, and preparation. Let’s explore the emerging trends shaping the future…
🔮 The Future of Cloud Security: 2025 Trends and Beyond
🤖 Trend #1: AI-Powered Defense Systems
Just as attackers are using AI, defenders are fighting fire with fire. AI-powered security systems can:
- Analyze millions of security events in real-time
- Predict attack patterns before they happen
- Automatically respond to threats without human intervention
- Learn from each attack to improve future defense
According to recent surveys, 63% of security professionals believe AI enhances their security capabilities, with threat detection being the primary use case.
🌐 Trend #2: Edge Security Revolution
As computing moves closer to users through edge computing, security must follow. This means protecting not just centralized cloud data centers, but thousands of smaller computing nodes distributed worldwide.
♻️ Trend #3: Sustainable Security
Environmental consciousness is reaching cybersecurity. Cloud providers are implementing green security practices that reduce energy consumption while maintaining protection levels. It’s proof that being environmentally responsible and security-conscious can go hand in hand.
🏛️ Trend #4: Regulatory Evolution
With Europe leading the charge through initiatives like GAIA-X and the NIS2 directive, data sovereignty and privacy regulations are becoming more stringent. Organizations must prepare for a future where data location and processing transparency are legal requirements.
🎯 As we wrap up our journey through the cloud security landscape, let’s focus on practical steps you can take today…
🚀 Your Cloud Security Action Plan: Getting Started Today
🏃♀️ Phase 1: The Security Sprint (Week 1)
Immediate Actions:
- Audit your current access: Who has keys to your digital kingdom?
- Enable MFA everywhere: No exceptions, no excuses
- Review your cloud configurations: Use free tools like AWS Config or Azure Security Center
- Update all passwords: Use a password manager to generate strong, unique passwords
- Check for public exposures: Scan for accidentally public storage buckets or databases
🏗️ Phase 2: Building Your Defenses (Month 1)
- Implement encryption: Start with data at rest, then tackle data in transit
- Set up monitoring: Deploy CSPM tools to watch for misconfigurations
- Create an incident response plan: Know what to do when (not if) something goes wrong
- Train your team: Security awareness isn’t just for IT professionals
- Regular security assessments: Schedule monthly security reviews
🏰 Phase 3: Fortifying Your Kingdom (Ongoing)
- Zero Trust implementation: Gradually move toward “never trust, always verify”
- Advanced threat detection: Deploy AI-powered security tools
- Compliance alignment: Ensure your security measures meet industry standards
- Continuous improvement: Learn from each incident and security assessment
🎯 Success Metrics to Track
- Mean Time to Detection (MTTD): How quickly you spot threats
- Mean Time to Response (MTTR): How fast you can respond to incidents
- Security Score: Overall posture rating from your CSPM tools
- Compliance Status: Percentage of controls meeting requirements
- User Security Awareness: Results from phishing simulations and training
🌟 As we conclude our epic journey through the cloud security landscape, remember that security isn’t a destination—it’s an ongoing adventure…
🎉 Your Cloud Security Journey Continues
Congratulations! You’ve just completed a comprehensive tour through the complex but fascinating world of cloud security. From understanding the shared responsibility model to exploring cutting-edge AI-powered defenses, you now have the knowledge to start protecting your digital kingdom like a true security champion.
Remember, cloud security isn’t about achieving perfection—it’s about continuous improvement, vigilant monitoring, and smart risk management. The threats will continue to evolve, but so will your defenses. With 61% of organizations experiencing cloud security incidents in 2024, those who master these fundamentals will have a significant advantage.
🔥 Key Takeaways for Your Cloud Security Success:
- Embrace the Partnership: Understand what you’re responsible for in the shared responsibility model
- Layer Your Defenses: Use encryption, MFA, and Zero Trust as your security foundation
- Stay Vigilant: Implement continuous monitoring with CSPM and CNAPP tools
- Learn from Others: Study real-world breaches to understand what not to do
- Plan for the Future: Prepare for AI-powered threats and emerging regulations
The cloud security landscape might seem daunting, but you’re not alone in this journey. Every security professional started where you are now—curious, eager to learn, and ready to build something secure and lasting.
🚀 Ready for your next adventure? Stay tuned for our upcoming article: “Cloud Cost Optimization: How to Save Money Without Sacrificing Security” where we’ll explore how to build robust defenses on any budget!
Keep learning, stay secure, and remember: In the ever-evolving world of cloud computing, your security knowledge is your most powerful weapon. Your digital kingdom awaits your protection—go forth and secure it! 🛡️✨

