🚨 EXPOSED: How Hackers Turned a Simple Chat App Into a Mega Data Heist
Hold onto your hats, folks! The cybersecurity world just got rocked by one of the most sophisticated supply chain attacks we’ve seen in 2025. What started as a simple AI chat app called “Drift” has turned into a massive data breach affecting some of the biggest names in tech – including cybersecurity giant Palo Alto Networks.
Here’s the kicker: this wasn’t your typical “hackers break down the front door” scenario. Instead, these digital criminals found a way to use legitimate business tools against companies, stealing massive amounts of customer data without anyone noticing for over 10 days. Ready to dive into this cyber thriller? Let’s unpack what happened and what it means for you!
💥 It all started with something as innocent as a customer chat app…
🎭 The Perfect Crime: How It All Went Down
Picture this: You’re running a massive tech company, and you use a popular AI chat app called “Drift” to help with customer engagement. It connects to your Salesforce system to access customer data and provide better support. Sounds normal, right? Well, that’s exactly what the hackers were counting on.
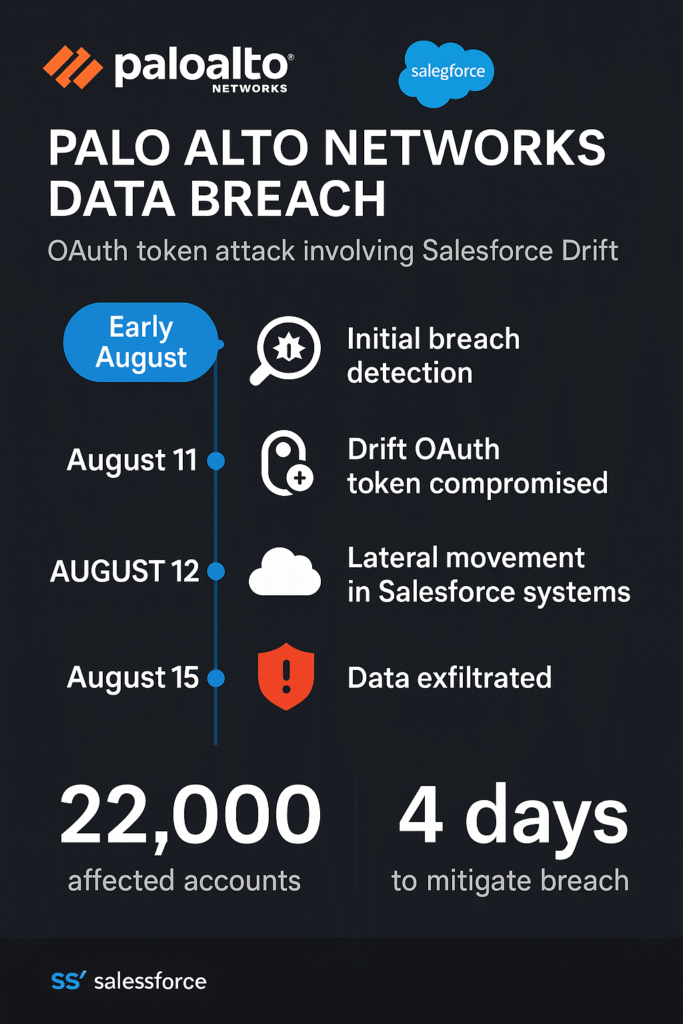
Between August 8-18, 2025, a group of cybercriminals that security experts call “UNC6395” pulled off something incredible. They managed to steal the digital keys (called OAuth tokens) that Drift uses to access company Salesforce accounts. Think of it like stealing a master key that opens every customer file cabinet in the building.
📅 The Attack Timeline: 11 Days of Silent Theft
August 8, 2025: Hackers begin stealing OAuth tokens from Drift’s systems
August 8-18: Mass data extraction from hundreds of Salesforce accounts begins
August 18: Attack campaign ends, logs deleted to cover tracks
August 20: Salesforce and Drift discover the breach, revoke all tokens
September 1: Palo Alto Networks publicly confirms they were hit
🏢 But who exactly got caught in this digital heist?
🎯 The Victims: Big Names, Big Problems
This wasn’t some small-time operation targeting mom-and-pop shops. The hackers went after the big fish, and they caught some whales. Here are the major companies that have confirmed they were hit by this supply chain attack:
🔥 Confirmed Victims:
- Palo Alto Networks: The cybersecurity giant that ironically got hacked – customer contact info and sales data stolen
- Zscaler: Another major cybersecurity company – customer names, contacts, and support case details compromised
- Google: Even the search giant wasn’t immune – some Workspace email data was accessed
- Hundreds of other companies: Security experts believe the total victim count is in the hundreds
What makes this particularly embarrassing is that two of the biggest names in cybersecurity – companies that literally sell protection against these kinds of attacks – got caught with their digital pants down. It’s like having your home security company get robbed!
📊 By The Numbers:
The attack lasted 11 days, affected hundreds of companies, and involved the theft of millions of customer records. The hackers used automated Python scripts to make the data theft faster and more efficient.
🤔 So what exactly did these digital thieves make off with?
💰 The Loot: What Got Stolen (And Why You Should Care)
Now, you might be thinking “Okay, so they stole some business contact information. Big deal, right?” Wrong! This is where the story gets really scary. The hackers weren’t just after email addresses and phone numbers – they had a much more sinister plan.
📋 The Stolen Data Included:
- Customer Contact Information: Names, emails, phone numbers, company details
- Internal Sales Data: Deal values, sales pipeline information, account details
- Support Case Information: Customer problems, internal notes, resolution details
- Business Communications: Internal emails and messages stored in CRM systems
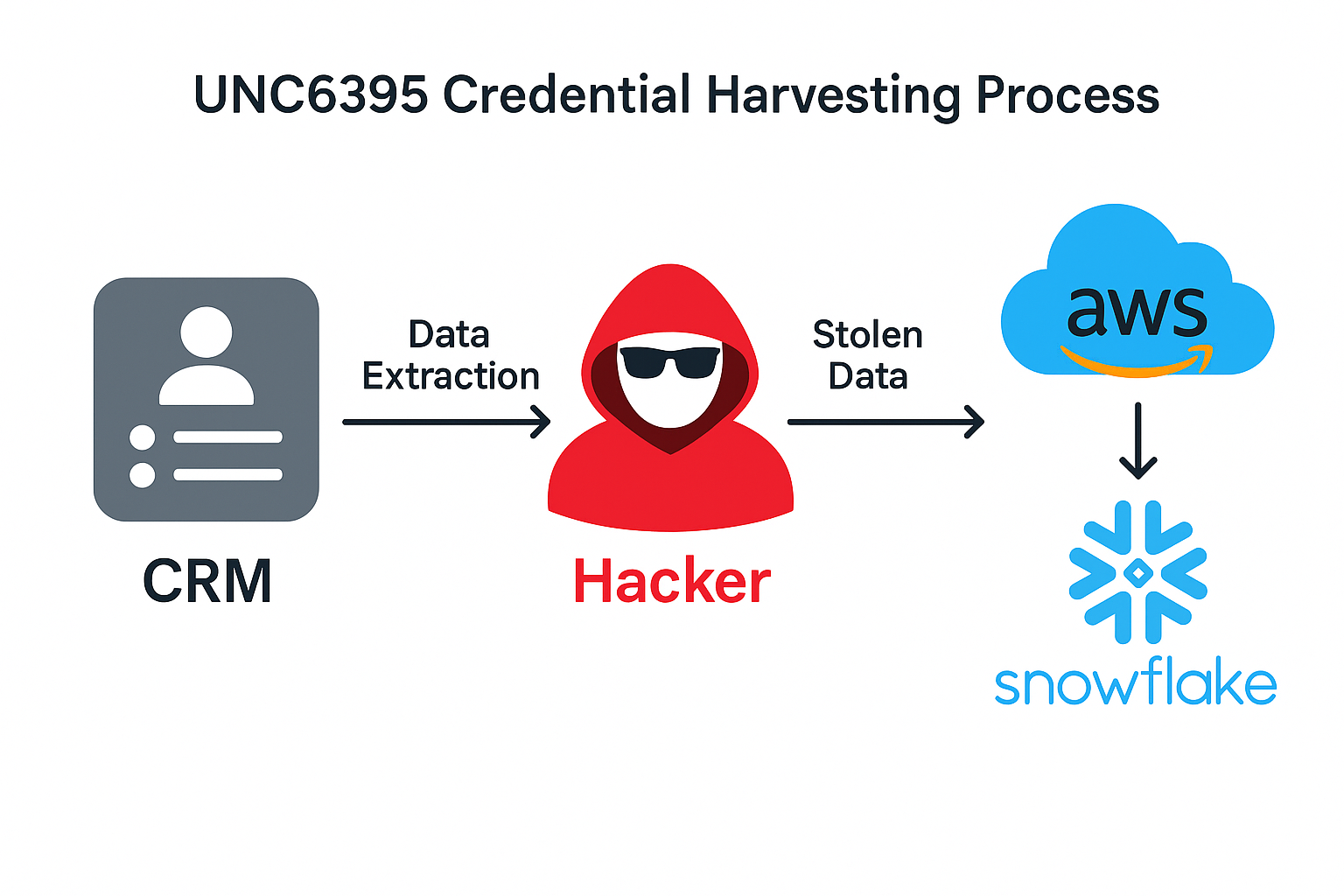
But here’s the truly terrifying part: the hackers weren’t planning to sell this data on the dark web or use it for spam. Instead, they were playing a much longer game. Security researchers discovered that the criminals were scanning the stolen data for hidden treasures – passwords, API keys, and access tokens for other services like Amazon Web Services and Snowflake.
“It’s like breaking into someone’s house to steal their address book, then using that information to figure out where they hide their spare keys to rob even more houses.” – Cybersecurity Expert
⚡ This technique, called “credential harvesting,” is what makes this breach so dangerous…
🕵️ The Master Plan: From CRM Theft to Cloud Takeover
What makes the UNC6395 group so dangerous isn’t just their technical skills – it’s their strategy. They understand that modern businesses store secrets everywhere, including in places you’d never expect, like customer support notes and sales records.
Think about it: how many times have you or your colleagues written down a password in an email, saved an API key in a document, or shared login credentials in a support ticket? All of that information lives in your CRM system, and that’s exactly what these hackers were hunting for.
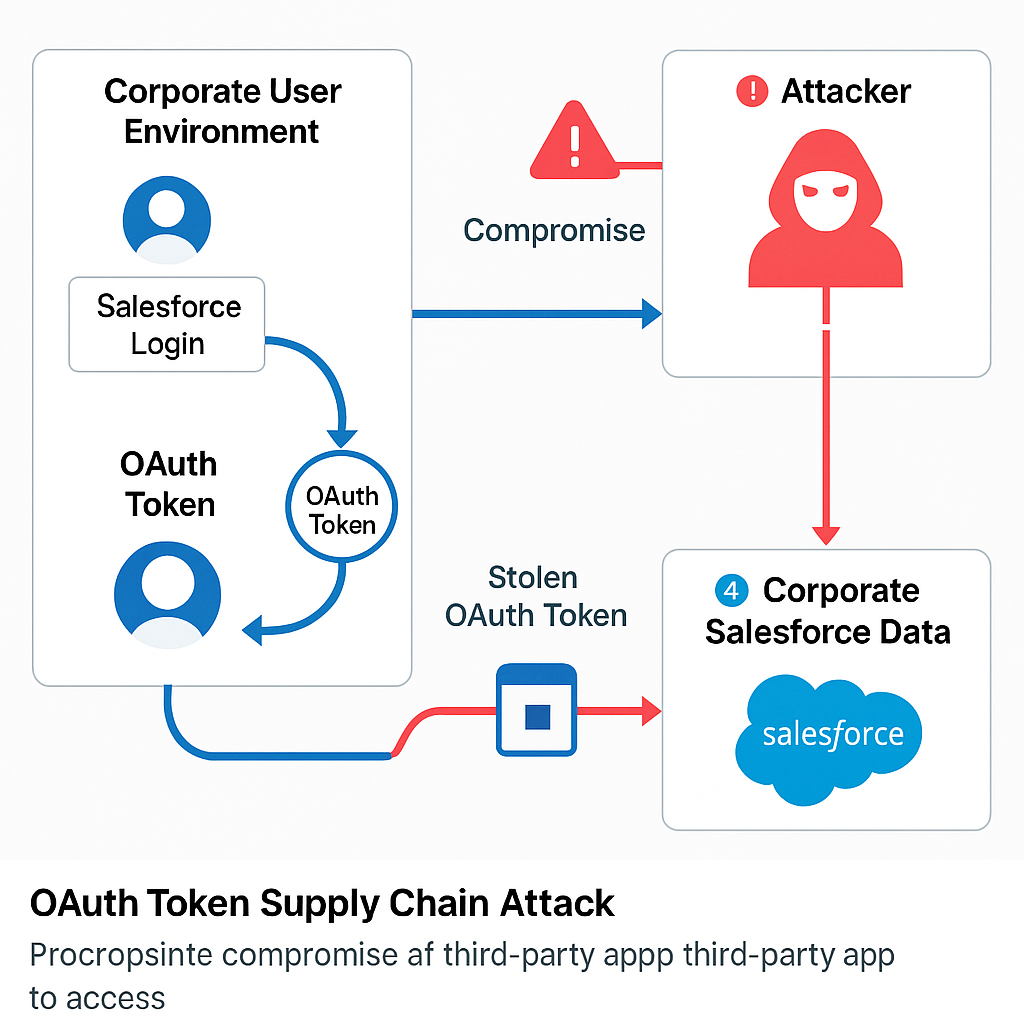
🎯 The Hacker’s Playbook:
- Step 1: Steal OAuth tokens from a trusted third-party app (Drift)
- Step 2: Use those tokens to access company Salesforce systems
- Step 3: Download massive amounts of CRM data automatically
- Step 4: Scan the data for passwords, API keys, and cloud credentials
- Step 5: Use found credentials to break into AWS, Snowflake, and other cloud services
- Step 6: Delete logs to cover their tracks and disappear
This multi-stage approach is what makes supply chain attacks so effective. Instead of trying to hack each company individually, the criminals compromised one trusted service provider and gained access to hundreds of companies at once. It’s efficient, scalable, and incredibly hard to detect.
🚨 So what’s being done to stop this digital disaster?
🛡️ The Response: How Companies Are Fighting Back
Once the breach was discovered, the response was swift and decisive. Both Salesforce and Salesloft (the company behind Drift) immediately went into crisis mode to contain the damage.
⚡ Immediate Actions Taken:
- Token Revocation: All OAuth tokens connected to Drift were immediately cancelled
- App Removal: Drift was temporarily removed from the Salesforce AppExchange marketplace
- Customer Notifications: Affected companies were contacted with detailed incident reports
- Security Patches: Both companies implemented additional security measures
Palo Alto Networks, despite being a victim themselves, immediately activated their elite Unit 42 security team to investigate the breach and share their findings with the broader cybersecurity community. It’s a classy move that shows how the good guys share information to protect everyone else.
🚨 What Palo Alto Networks Said:
“We want to be clear: this incident did not affect any of our products or services. Our security infrastructure remained fully intact. The exposure was limited to business contact information in our CRM system through the compromised Drift integration.”
💡 This leads to the million-dollar question: how can you protect your business from similar attacks?
🔐 Your Defense Playbook: How to Stay Safe
The scary truth is that if cybersecurity giants like Palo Alto Networks and Zscaler can get caught by this type of attack, anyone can. But don’t panic! There are specific steps you can take right now to protect your business from similar supply chain attacks.
🚀 Immediate Action Items (Do This Today):
For Salesforce Users:
- Audit Your Connected Apps: Go to Setup → Connected Apps and review every single integration
- Remove Unused Apps: If you don’t recognize it or don’t use it, disconnect it immediately
- Check Permissions: Make sure apps only have access to the data they actually need
- Review Recent Activity: Look for unusual data exports or API activity in August 2025
- Rotate Credentials: Change any passwords or API keys stored in your CRM data
For Everyone Else:
- Inventory Your SaaS Apps: Make a list of every cloud service your business uses
- Review App Permissions: Check what data each service can access
- Implement Least Privilege: Give apps the minimum access they need to function
- Monitor API Activity: Set up alerts for unusual data download patterns
- Train Your Team: Make sure everyone understands not to store passwords in CRM notes
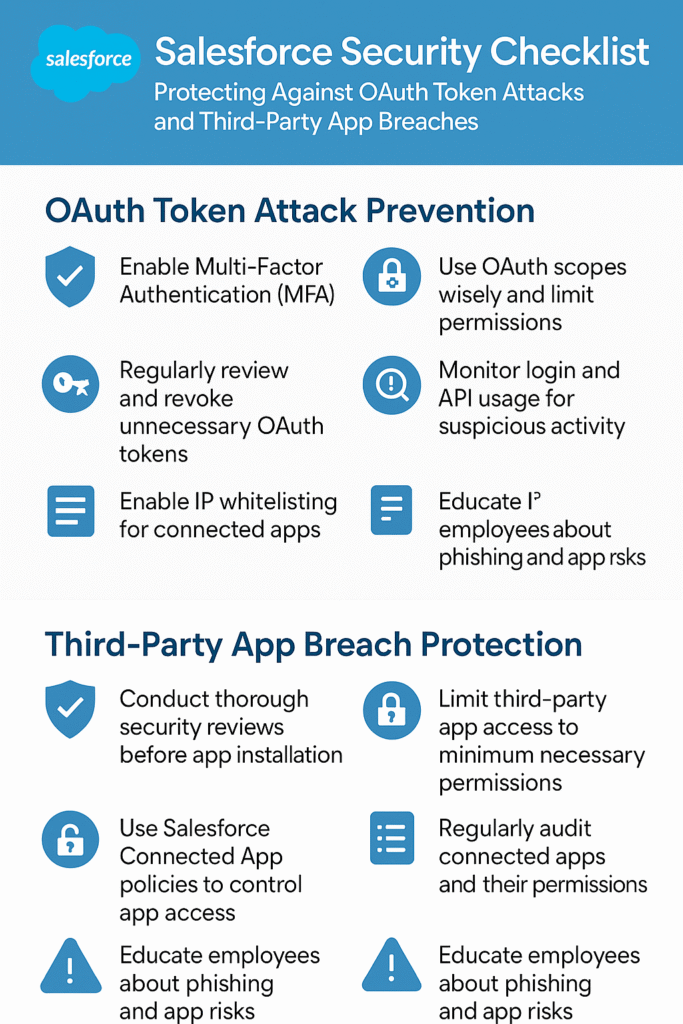
🏰 Long-Term Defense Strategy:
Building a defense against supply chain attacks isn’t just about technology – it’s about changing how you think about trust and security in the cloud era.
- Zero Trust Everything: Don’t automatically trust any service, even if it’s “legitimate”
- Continuous Monitoring: Set up systems to watch for unusual data access patterns
- Regular Security Audits: Review your connected apps and permissions quarterly
- Incident Response Planning: Have a plan ready for when (not if) you get breached
- Vendor Risk Management: Evaluate the security practices of every service you use
🌟 As we wrap up this cyber thriller, let’s talk about what this means for the future…
🔮 The Future: What This Breach Means for Everyone
The Drift-Salesforce breach isn’t just another news story – it’s a wake-up call that should fundamentally change how businesses think about cloud security. We’re living in an era where your biggest security risk might not be a hacker trying to break down your front door, but a criminal who already has the keys to your neighbor’s house.
🎯 Key Takeaways:
- Supply chain attacks are the new normal – expect more of these in 2025
- OAuth tokens are valuable targets – protect them like crown jewels
- CRM data contains hidden secrets – audit what’s stored there
- Even security companies get hacked – nobody is immune
- Fast response limits damage – have an incident plan ready
🚨 The New Reality Check
This attack proves that in 2025, cybersecurity isn’t just about protecting your own systems – it’s about understanding and managing the security risks of every vendor, app, and integration you use. The old approach of “trust but verify” needs to become “never trust, always verify, and verify again.”
Companies need to start treating third-party integrations like potential security vulnerabilities rather than convenient business tools. Every app permission should be justified, every data access should be monitored, and every integration should be regularly audited.
🎉 Ready to take action and protect your business? Here’s your next step…
⚡ Your Mission (If You Choose to Accept It)
Don’t let this story be just another “wow, that’s scary” moment that you forget about tomorrow. The companies that will survive and thrive in our interconnected digital world are the ones that take proactive steps to secure their supply chains today.
🎯 Your 30-Day Security Challenge:
- Week 1: Audit all your connected apps and remove unused integrations
- Week 2: Review and tighten app permissions across all your cloud services
- Week 3: Implement monitoring for unusual data access patterns
- Week 4: Train your team on secure data handling practices
Remember, the UNC6395 hackers succeeded because they understood that modern businesses are only as secure as their weakest integration. Don’t let that weak link be in your organization.
The digital world is full of opportunities, but it’s also full of digital predators looking for their next victim. By learning from what happened to Palo Alto Networks, Zscaler, and hundreds of other companies, you can make sure your business doesn’t become the next headline in a cyber breach story.
💪 Stay vigilant, stay secure, and remember: in cybersecurity, paranoia is just good planning!
The age of “it won’t happen to us” is over. The age of proactive security starts now. Your customers, your employees, and your business deserve nothing less than your best effort to keep their data safe! 🔒✨
Reference: https://cybersecuritynews.com/palo-alto-networks-data-breach/
